Xiomara CTF 2018: Dig Deep
Challenge details
| Event | Challenge | Category | Points | Solves |
|---|---|---|---|---|
| Xiomara CTF 2018 | Dig Deep | Forensic | 150 | ¯\(ツ)/¯ |
Download: Google Drive
TL;DR
If you are not interested in the detailed answer to the question “How to solve this problem?”, the short answer is that you should never trust the file deletion process and ensure that you perform secure file deletion, especially for sensitive files or data.
Having quickly identified deleted files from on a file carving process, digging a little deeper, we were able to get access to confidential data.
Methology
Download archive and extract it:
# 7z x private.7z
The archive seems to contain a disk image, let’s check it:
# file private.dd
private.dd: DOS/MBR boot sector, code offset 0x3c+2, OEM-ID "mkfs.fat", sectors/cluster 4, root entries 512, Media descriptor 0xf8, sectors/FAT 200, sectors/track 32, heads 64, sectors 204800 (volumes > 32 MB), serial number 0x2e594bed, unlabeled, FAT (16 bit)
Let’s recover all files from this volume (including deleted ones):
# foremost -i private.dd -o out/
What an interesting output, it seems that this volume contains a git repository:
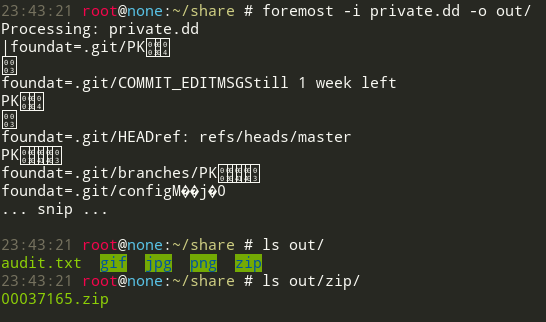
A significant part of data consists of JPEG image files, let’s check the EXIF data for useful information:
# find out/ -type f -exec exiftool {} \;
Nothing interesting here, let’s check the other files…
We finally found that the repository is located in a ZIP file:
# unzip out/zip/00037165.zip -d git/
# pushd git/
Let’s checkout branches and commits of this repository:
# git branch -a -vv
* master 1096fc8 [origin/master: en avance de 5] Still 1 week left
remotes/origin/HEAD -> origin/master
remotes/origin/master 75f9b8f Initial commit
# git log -u
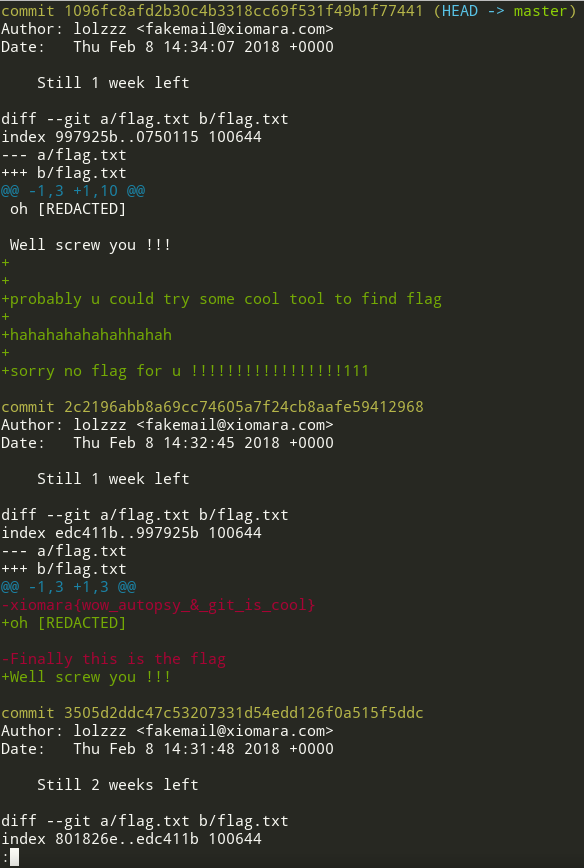
Here we got the flag!
Final flag:
xiomara{wowautopsy&_git_is_cool}
Creased
