NDH 2018 - ICMP
| Event | Challenge | Category | Points | Solves |
|---|---|---|---|---|
| Nuit du hack 16 | ICMP | Forensic | 50 | ¯\(ツ)/¯ |
Description
This forensic / network challenge is made by WorldCitizen for the 16th edition of Nuit du hack (NDH). In this task we are going to deal with ICMP packet in a pcap. You can find the ressource here: analysis.pcap
TL;DR
As I said before, we got a pcap file with approximatly 50 icmp packets. In each packet we can see base64 encoded data.
Then with a little on-liner based on tshark, I was able to get the flag :-)
Extraction
So, I start with this pcap:
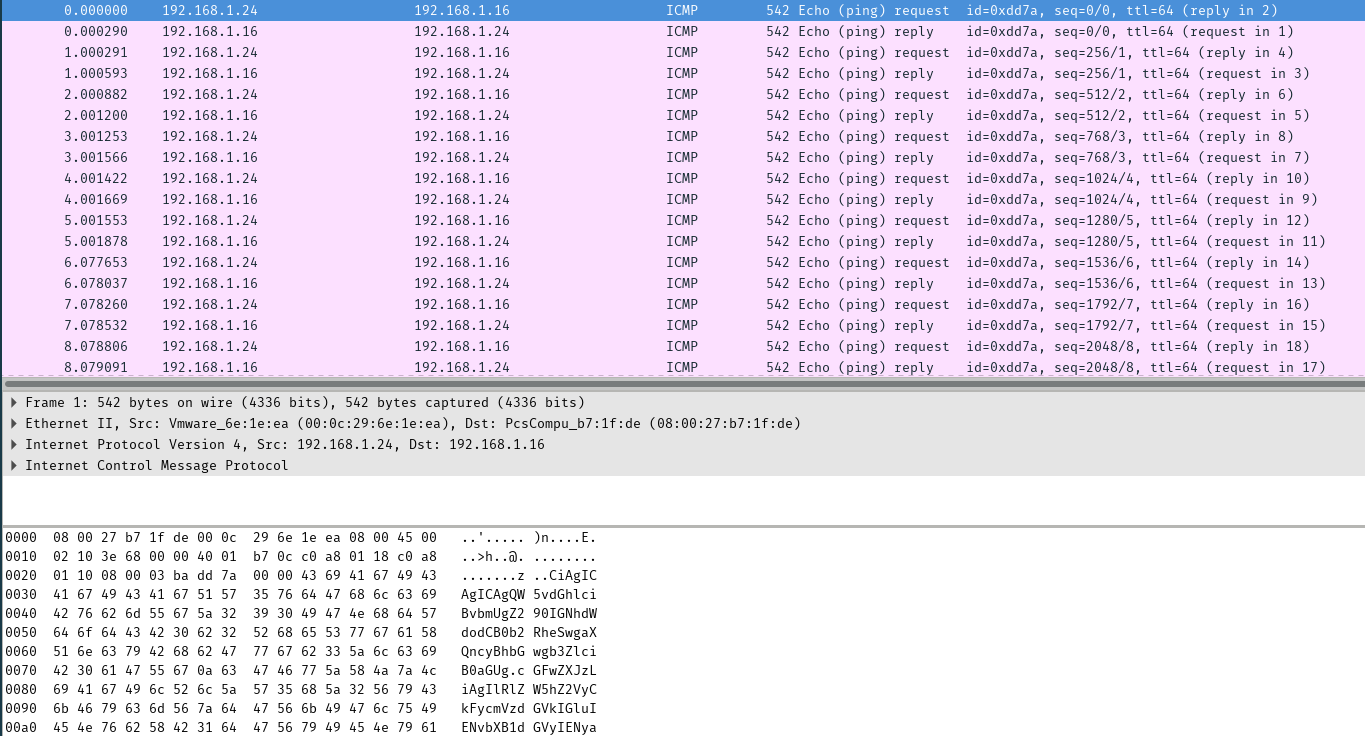
Fig 1 - ICMP packet with base64 encoded data
I just wanted to get all icmp request, so to do that I… Filtered on IP source instead of read the manual :-D
But it worked with this command:
tshark -2 -r analysis.pcap -R "ip.src == 192.168.1.24" -T fields -e data | xxd -r -p
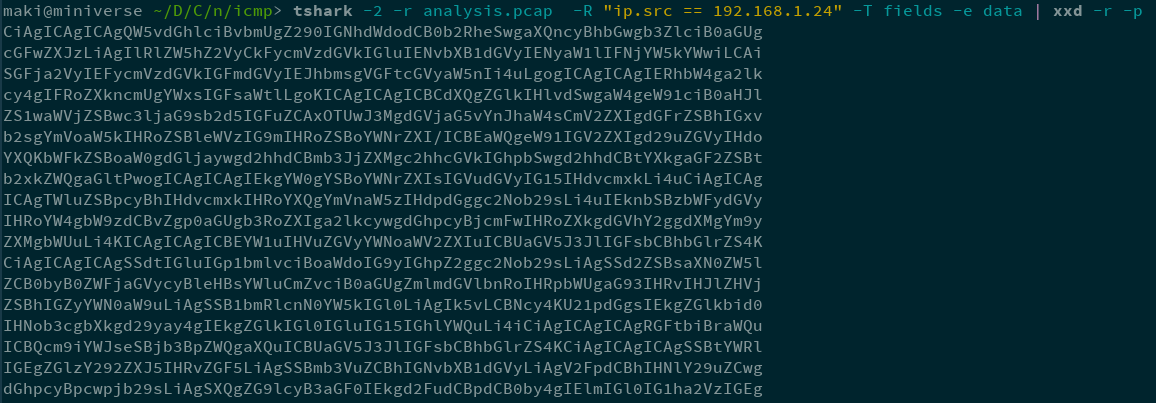 Fig 2 - Get the base64 !
Fig 2 - Get the base64 !
The xxd command is here to unhex the content. In fact, tshark will give the hexadecimal value of the field data.
Flag
Then, time to flag:
tshark -2 -r analysis.pcap -R "ip.src == 192.168.1.24" -T fields -e data | xxd -r -p | base64 -d | grep 'ndh'
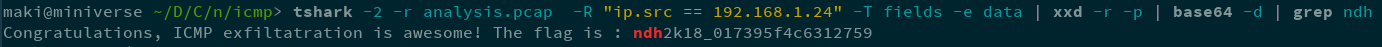 Fig 3 - w00t \o/
Fig 3 - w00t \o/
ndh2k18_017395f4c6312759
Maki
