Challenge details
| Event | Challenge | Category | Points | Solves |
|---|---|---|---|---|
| TamuCTF 2019 | ReadingRainbow - 1_Discovery | Forensic | 100 | 263 |
Download: capture.pcap - md5: e36ff23c6995e3595035982cced6c6a9
Description
- What is the IP address of the host exfiltrating data?
- For how long did the exfiltration happen? (Round to the nearest second. Format: MM:SS)
- What protocol/s was used to exfiltrate data? (Alphabetical order, all caps, comma separated, with spaces - ex: ABCD, BBCD)
Difficulty: easy
2⁄23 1:55 am Add extra info to 3
capture.pcap - md5: e36ff23c6995e3595035982cced6c6a9
TL;DR
I used wireshark and identified DET data into ICMP requests.
Methology
It’s time to open this big PCAP file in Wireshark. Thanks to the first question, we know that the attack exfiltrates some data. The best filter for that is still: data.data:
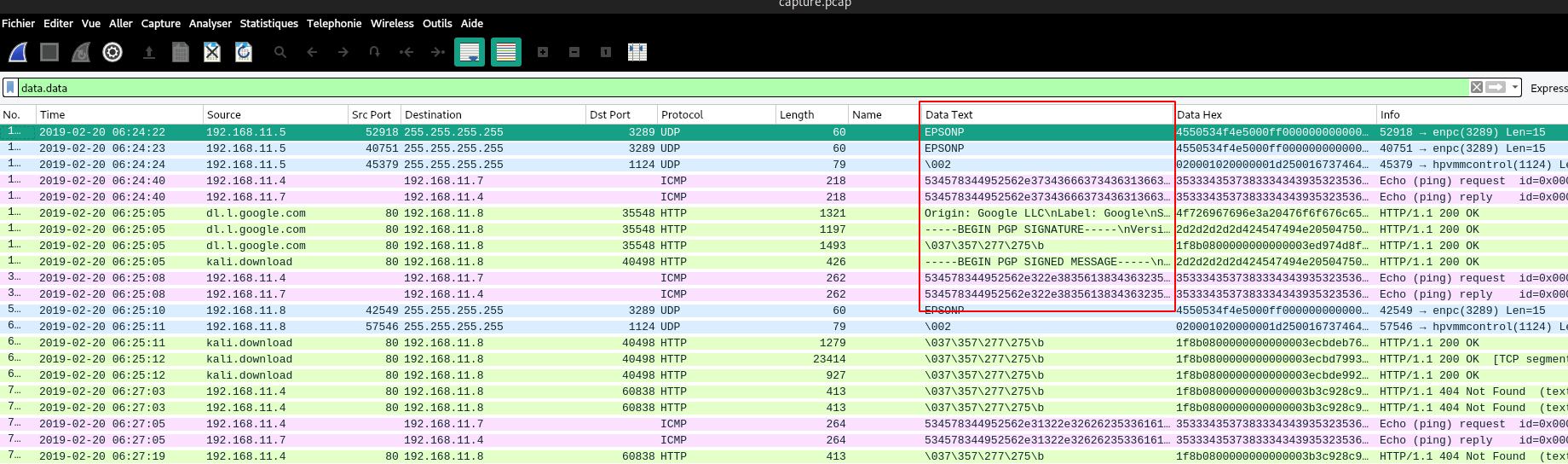
Fig 1: Suspicious ICMP traffic
We can see that our web server (192.168.11.4) is chatting with another host (192.168.11.7) via weird ICMP requests. Let’s see what these requests contain:
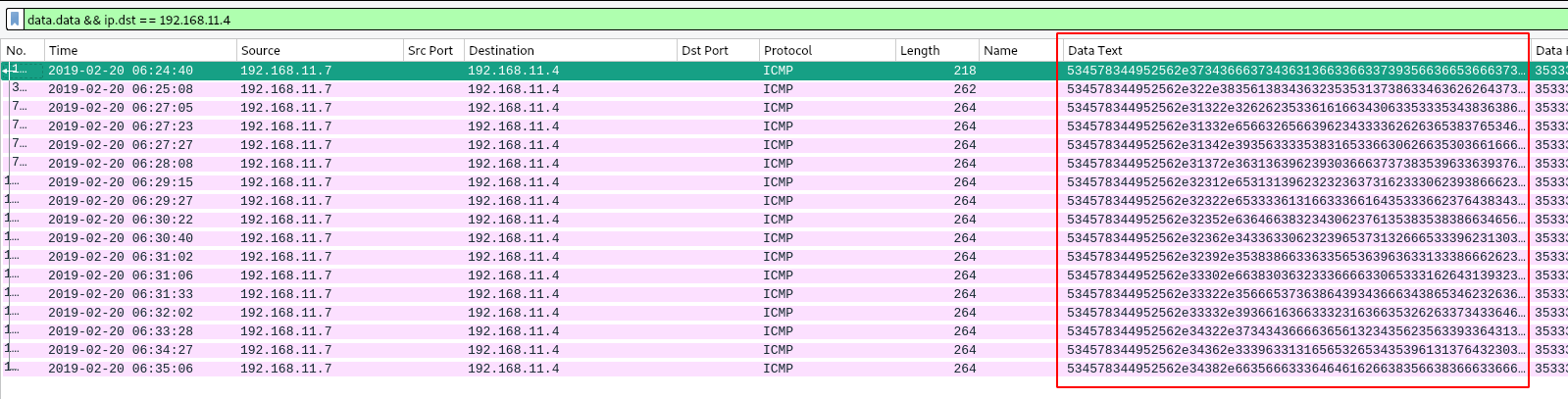
Fig 2: Filter on data
If we get the first request with a tshark:
▶ tshark -r capture.pcap -Y "data.data && ip.dst == 192.168.11.4" -Tfields -e 'data.text' | head -n 1 | xxd -r -p
SEx4IRV.746f74616c6c795f6e6f7468696e672e706466.REGISTER.6156eab6691f32b8350c45b3fc4aadc1
The data formatted like this looks a lot like the DET (Data Exfiltration Toolkit) framework. I had already talked about it in a writeup at the SantHackLause 2018.
Flag 1: 192.168.11.7
Now we have to determine the duration of the exfiltration. With a small filter on IPs, we see some interesting things in the DNS:
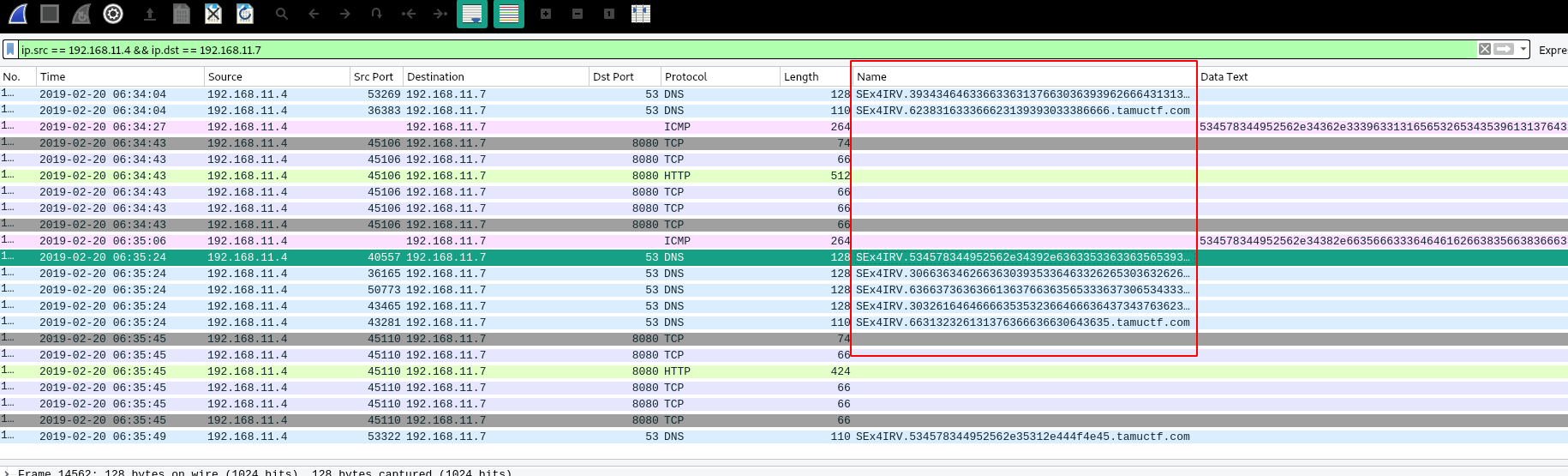
Fig 3: Suspicious domain name
If we extract the last DNS request and this is indeed the last DET request, we should find a “DONE”:
▶ echo -n '534578344952562e35312e444f4e45' | xxd -r -p
SEx4IRV.51.DONE
Perfect, we know the first request with the “REGISTER” and the last one with the “DONE”.

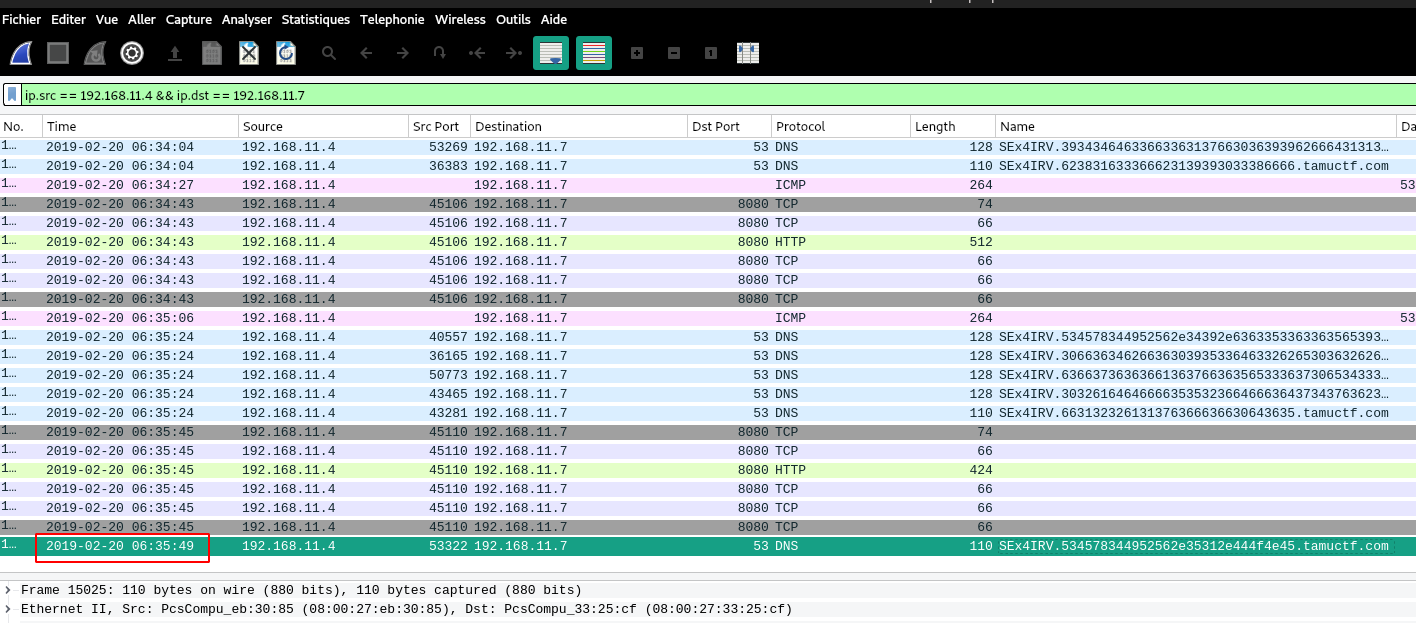
Fig 4: Timestamp
▶ echo $((35.49-24.40))
11.090000000000003
The exfiltration lasted 11 minutes and 9 seconds:
Flag 2: 11.09
The last step will be the simplest, we already have all the information, to find the protocols, we will do a little tshark trick:
▶ tshark -r capture.pcap -Y "ip.src == 192.168.11.4 && ip.dst == 192.168.11.7" -Tfields -e '_ws.col.Protocol' | sort | uniq
DNS
HTTP
ICMP
TCP
The “TCP” protocol is not counted since it is a transport protocol (see OSI Model).
Flag 3: DNS, HTTP, ICMP
Flag
192.168.11.7
11.09
DNS, HTTP, ICMP
